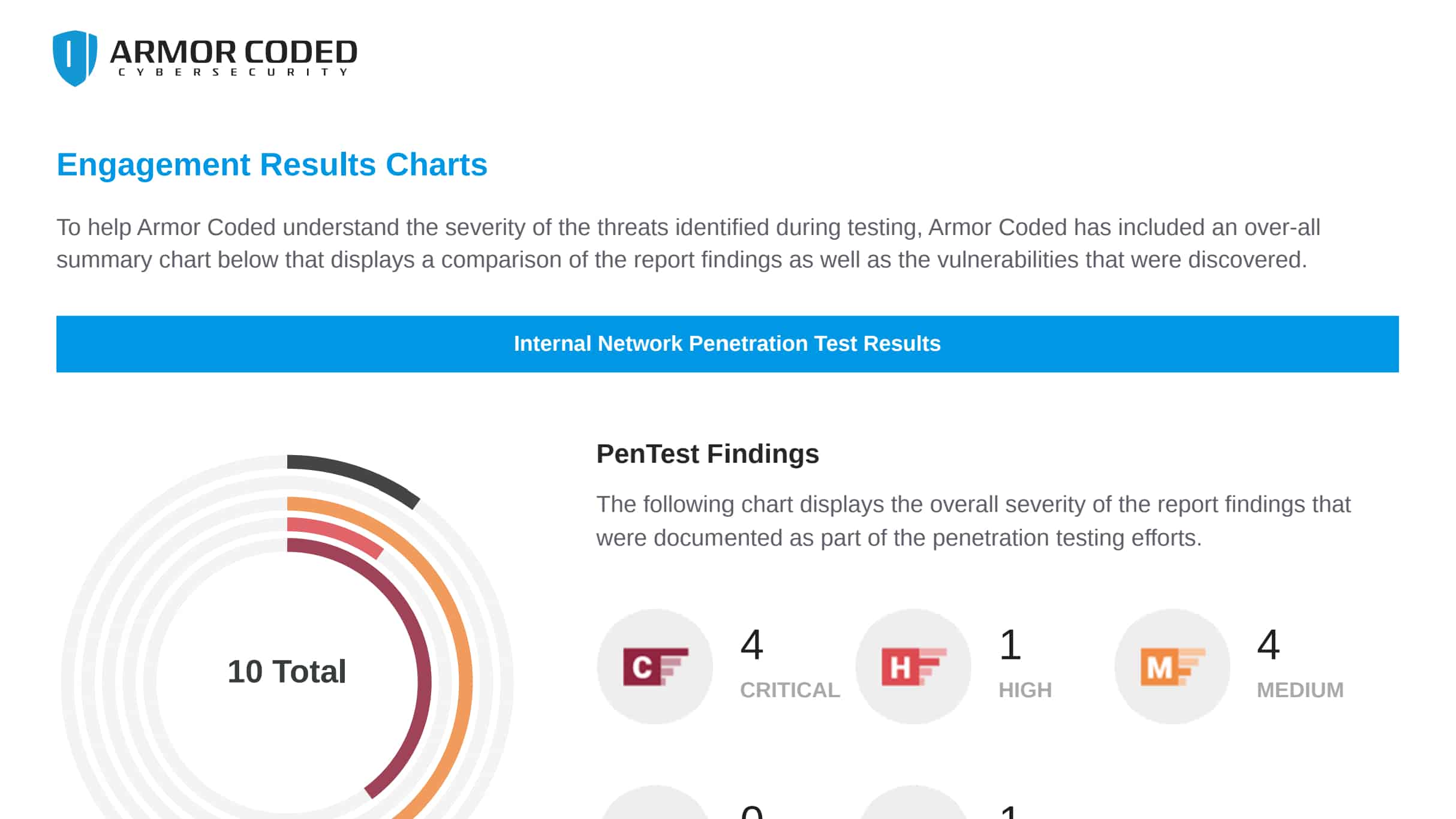
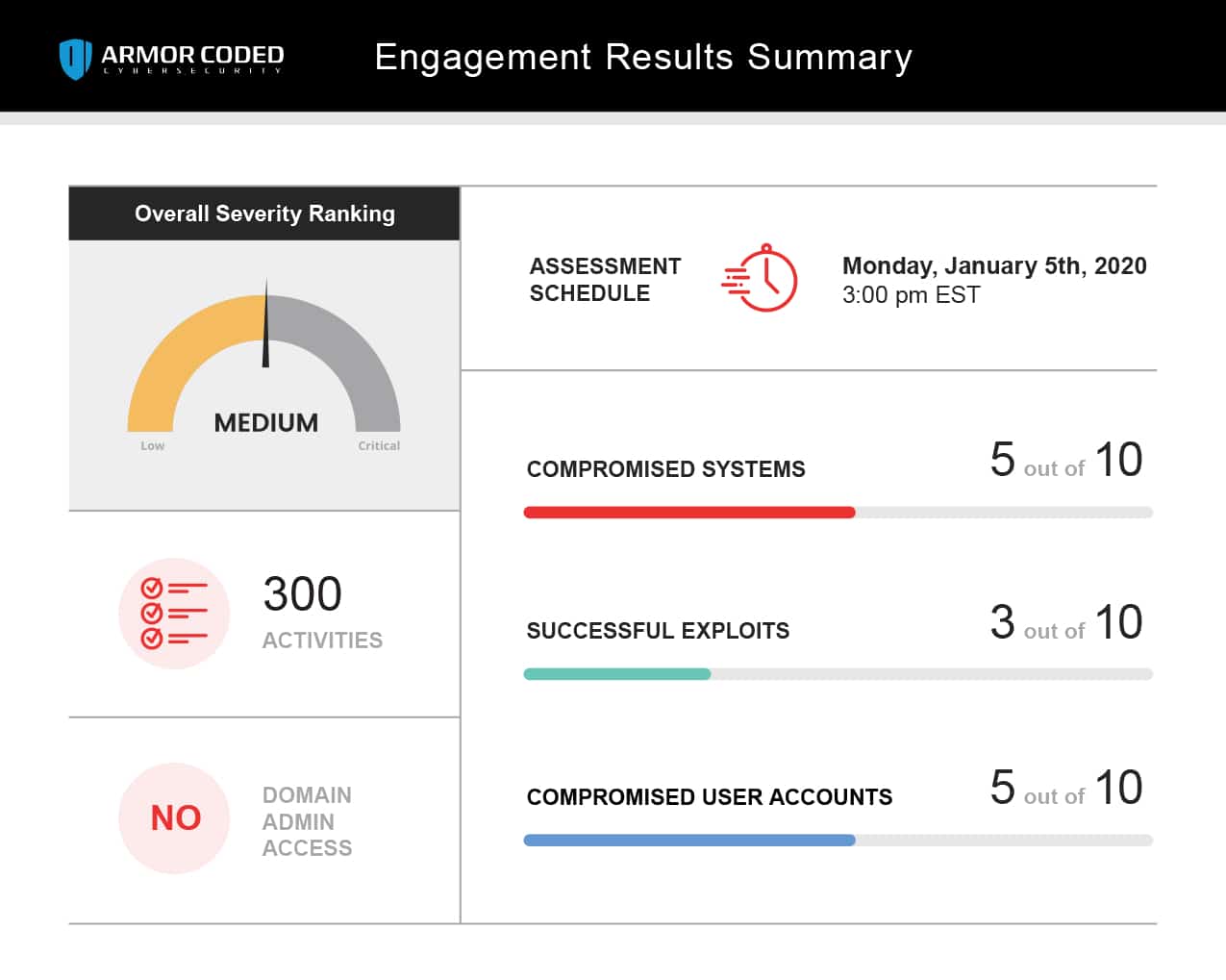
Discover what a hacker sees on your network before they do.
Network penetration testing is a comprehensive test to see how safe and secure your organization is from all angles. We’ll look at how well you can handle different threats and if you’re ready for any potential breaches.
Our goal is to show you how effective your current controls are, and to identify any vulnerabilities that may be there.