In the age of smart living, our homes are becoming increasingly intelligent. They’re designed to cater to our every need...
There is no escaping the relentless march of AI. Software companies are rapidly incorporating it into many business tool...
In a world where technology constantly evolves, Microsoft stands at the forefront. It continues to pioneer innovations. ...
Cybersecurity has become a critical foundation upon which many aspects of business rely. Whether you’re a large enterpri...
The use of AI-driven processes is exploding. Every time you turn around, software has gotten more intelligent. Harnessin...
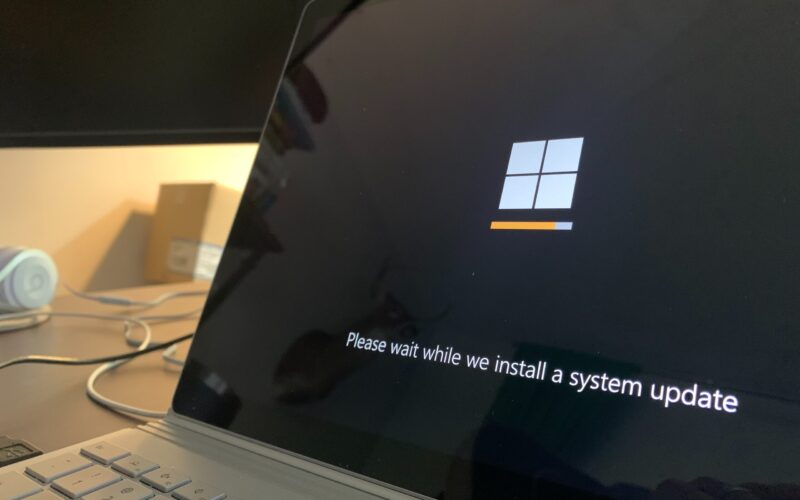
Imagine you’re working away on your PC and see a Windows update prompt. Instead of ignoring it, you take action. After a...
In today’s world, sustainability isn’t just a buzzword; it’s a necessity. Businesses around the globe ...
Smart homes have become a ubiquitous part of modern living. It doesn’t even seem unusual anymore to tell your refrigerat...
Software-as-a-Service (SaaS) has revolutionized the way businesses operate. It offers convenience, scalability, and effi...
Cybercriminals can launch very sophisticated attacks. But it’s often lax cybersecurity practices that enable most breach...
Endpoint management has changed a lot over the last two decades. There was a time when companies housed all endpoints in...
Two monitors are often better than one when it comes to getting things done efficiently. A dual-monitor setup can signif...
Let’s dive into a topic that might give you the chills—cybersecurity skeletons in the closet. You may not have old skele...
As technology continues to advance, so does the need for heightened awareness. As well as proactive measures to safeguar...
Most people are familiar with their device’s Airplane Mode. You’ve probably used it when jetting off to exotic loc...
Apple’s iOS updates have always been eagerly anticipated. iPhone and iPad users around the world get excited to se...
Running a small business can be challenging. But advancements in technology have opened a world of opportunities. Small ...
Do you find budgeting for IT challenging? If so, you aren’t alone. While the IT budgeting process can be tricky for s...
Are you considering all the necessary technology categories when planning your annual budget? Technology is essential...
Are you planning to include your IT needs in your annual budget this year? If so, congratulations! You’re doing so...